
This year, major hacking incidents have continually made headlines. As news spreads about companies suffering from data breaches and ransomware attacks, many security managers have likely thought the same thing: “Are we next?”
Every security professional knows: The question isn’t if we’ll get hacked, but when.
[The Daily Reality of Security Teams Security teams]
The Daily Reality of Security Teams Security teams regularly conduct penetration tests, monitor CVE updates, and manage patch schedules.
*CVE (Common Vulnerabilities and Exposures): A system assigning unique identifiers to publicly known vulnerabilities for systematic management.
Yet, concerns persist:
“We have hundreds of servers, how can we track what software is installed on each?”
“Vulnerability scanners produce thousands of results. How do we know what to fix first?”
“If a patch causes downtime, I’m the one accountable. How can I confidently update?”
“During ISMS audits, I lose an entire week preparing documents. When can I actually do security work?”
The reality is always like this.
Management demands stronger security, but budgets and staff never meet the need. Developers push back: “If the patch disrupts the service, will you take responsibility?” The burden falls on security teams, leaving them overwhelmed about where to start.
[Government Oversight Strengthened]
On October 22, the government announced a Comprehensive Inter-Agency Cybersecurity Plan with these key measures:
-Full review of over 1,600 critical IT systems
-Mandatory submission of SBOMs (Software Bills of Materials)
-Stronger ISMS certification
Beyond paperwork, on-site audits will increase.
In short, the government wants real, effective security measures. But the real question is: how? Manually entering each server, listing packages, checking versions, and matching them to the CVE database- that’s not feasible.
Ultimately, everything boils down to one thing: “You can only defend what you know exists in your system.”
Hackers rarely take the hard route.
Rather than using zero-day exploits, they attack known vulnerabilities.
-The DirtyCow Linux kernel flaw was discovered in 2016
-Windows Server 2008, whose support ended in January 2020.
-Outdated libraries that developers installed years ago and forgot about.
The real issue is ignorance- not knowing where these weak points are.
If you don’t know what software runs on your servers, you can’t tell which vulnerabilities pose a threat.
[Five-Step Strategy for Vulnerability Management]
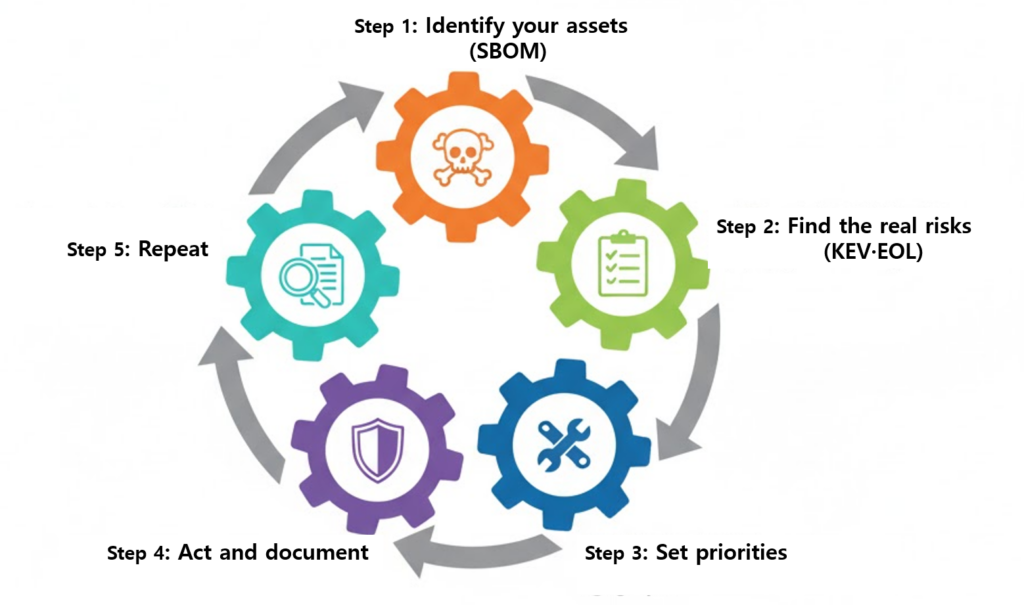
Step 1: Identify your assets (SBOM).
Create a full inventory of your environment.
OS(Operating System), applications, libraries, and versions.
*SBOM (Software Bill of Materials): is a “Software parts list” that records all components, libraries, and dependencies in a machine-readable format. It is essential for improving software supply chain transparency, detecting vulnerabilities, managing licenses, ensuring compliance, and simplifying software maintenance.
Step 2: Find the real risks (KEV and EOL).
Focus on known exploited vulnerabilities (KEV) and End-of-Life (EOL) software.
*KEV (Known Exploited Vulnerabilities): A catalog of vulnerabilities actively being exploited, managed by the U.S. CISA. About 1,400 out of more than 300,000 CVEs fall into this category.
*EOL (End of Life): Products or software that no longer receive official updates or support.
*CISA (Cybersecurity and Infrastructure Security Agency): A U.S. government agency under the Department of Homeland Security responsible for cybersecurity and infrastructure protection.
Step 3: Set priorities
It’s impossible to fix everything at once.
Start with internet-facing systems and high-risk vulnerabilities.
Step 4: Act and document
Patch vulnerabilities or apply mitigation measures, and record the actions for audit verification.
Step 5: Repeat
New vulnerabilities appear daily. Automation is essential.
Security teams understand this in theory, but lack time, manpower, and proper tools.
So, the question remains: “Can’t there be an easier way?”
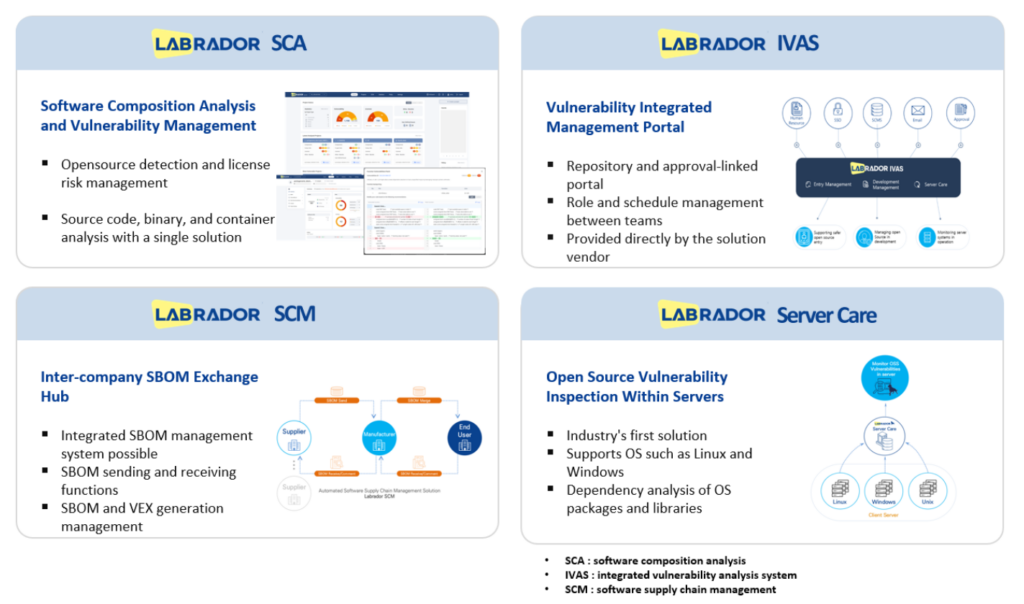
Labrador Labs: Solving Security Teams’ Pain Points Labrador Labs was founded to answer that very question. Its solutions address the toughest challenges facing security teams.
Challenge 1: “We have too many servers to know what’s installed.”
→ Automated asset scanning and instant SBOM generation
Simply install a single lightweight agent.
-Automatically collects OS, packages, libraries, and versions from all servers
-Displays real-time, auto-updated SBOMs on a dashboard
-Allows one-click SBOM file exports for regulatory submissions
Challenge 2: “There are hundreds of new CVEs every day, which ones matter to us?”
→ Automatic KEV and EOL matching with risk prioritization
Labrador identifies only vulnerabilities that genuinely affect your environment.
-Cross-checks with CISA’s KEV list in real time
-Detects unsupported (EOL) software
-Automatically prioritizes threats combining high privilege, external exposure, and KEV vulnerabilities.
Challenge 3: “We waste a week creating reports for every audit or certification.”
→ One-click compliance reporting
-Current vulnerability status by priority Patch
-Remediation evidence
-SBOM files for government compliance
-Server and date-specific customized reports
Security managers shouldn’t wake up each morning wondering, “What critical vulnerability will drop today?” With the right tools and automation, teams can focus on truly strategic security work.
📌 Get started now! Labrador Labs
Phone: US Office +1 650-278-9253 (Mon-Fri 09:00–18:00)
Email: contact@labradorlabs.ai
Contact us for 1:1 demos and quote!

