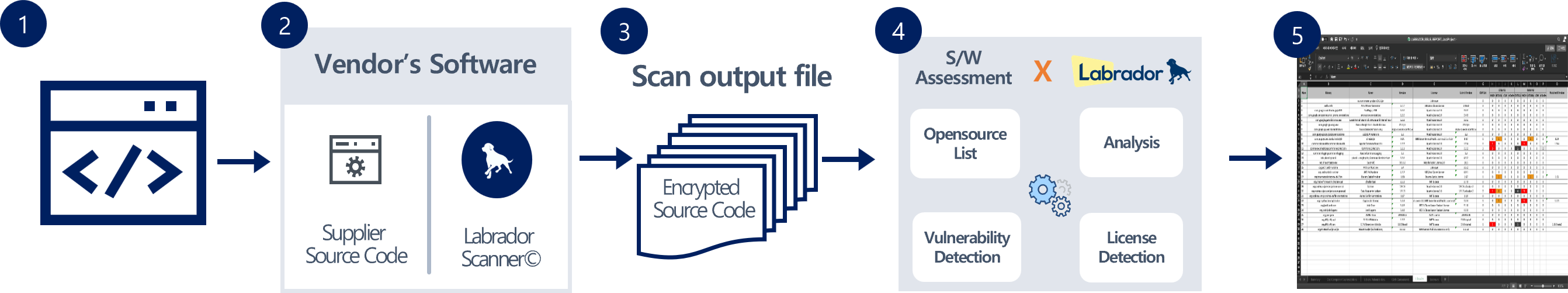
-
Step 1
The Labrador scanner is provided to your suppliers to scan their source code.
-
Step 2
After installing the Labrador Scanner, the suppliers' file will be encrypted.
-
Step 3
The scan output file is deciphered for you through your Labrador Interface.
-
Step 4
Through the Labrador Engine, the encrypted source code will be analyzed for vulnerabilities and licenses issues.
-
Step 5
A compiled file will be generated with all the information (SBOM, licenses violations and vulnerabilities).
Analyze suppliers' software while safeguarding code privacy!