It’s now harder to find a web development team not using React than one that does.
React, an open-source JavaScript library created by Meta (formerly Facebook), has become the standard technology
for modern web frontend development.
The problem is that what used to be just a “frontend library” has now become the gateway to the server itself,
All because of the recently disclosed Remote Code Execution (RCE) vulnerability in React Server Components (RSC),
known as React2Shell (CVE-2025-55182), which was made public on December 3.
[ As serious as Log4Shell ]
Security experts consider React2Shell the most impactful vulnerability since 2021’s Log4Shell (the Log4J flaw).
Like Log4Shell, React2Shell affects a widely used technology.
According to the 2024 State of JavaScript survey, 82% of developers reported using React, and the React package records over 20 million downloads per week.
A report from the cybersecurity company Wiz states that roughly 39% of cloud environments contain systems vulnerable
to this flaw. Popular frameworks such as Next.js and Remix are all React-based and thus at risk.
But the attack complexity is even lower than Log4Shell.
While Log4Shell required certain preconditions, React2Shell can be triggered over a network, involves little complexity,
requires no authentication, and no user interaction-attackers can compromise a server with a single HTTP request.
That’s why it received the top CVSS score of 10.0.
Attacks followed immediately
According to AWS Threat Intelligence, China state-sponsored hacking groups began exploiting the public proof-of-concept
within hours of its release.
Within a week, researchers observed diverse campaigns of cryptocurrency mining, credential theft, and backdoor deployments spreading faster than any Log4Shell exploitation.
[ What exactly is wrong with React2Shell? ]
The vulnerability exploits a structural flaw in the Flight protocol, which is used by React Server Components.
It’s not due to misconfiguration or a specific faulty feature; it’s a fundamental design flaw in the protocol itself.
Groups linked to China (like Earth Lamia and Jackpot Panda) are already conducting active attacks.
On December 5, the U.S. CISA urgently added React2Shell to its Known Exploited Vulnerabilities (KEV) catalog.
According to AWS, React 19.x, Next.js 15.x/16.x, and App Router based services are all vulnerable.

[ The Korean incidents show a bigger danger: neglect ]
The real threat of React2Shell isn’t just the vulnerability itself- it’s how unmanaged vulnerabilities cause massive breaches when left unpatched.
We’ve seen this pattern before.
- Lotte Card left a vulnerability unpatched that should have been fixed in 2017, leading to the leak of 1.28 million users’ personal data.
- SK Telecom failed to apply the DirtyCow Linux kernel patch for over 8 years, resulting in 23 million users’ data and USIM authentication keys being stolen.
The common lesson is clear: these weren’t caused by complex zero-days but by failure to apply known patches in time.
React2Shell could easily follow the same path.
[ The real question: do you even know if you’re exposed? ]
The biggest issue is that many organizations don’t even know whether their servers are vulnerable.
While security checks happen during development, once the service is deployed, the diligence fades.
Teams often scan for vulnerabilities only when software is first installed, but fail to track subsequent updates, library additions, or emergency patches.
Responsibility between operations, development, and security teams is often blurred leaving servers unmonitored while known vulnerabilities pile up.
Few companies maintain an up-to-date list of vulnerabilities for their live production servers.
If you can’t immediately answer “Which of our servers use vulnerable versions of React or Next.js?”, then you’re already in dangerous territory.
[ Solution: find real vulnerabilities in live servers ]
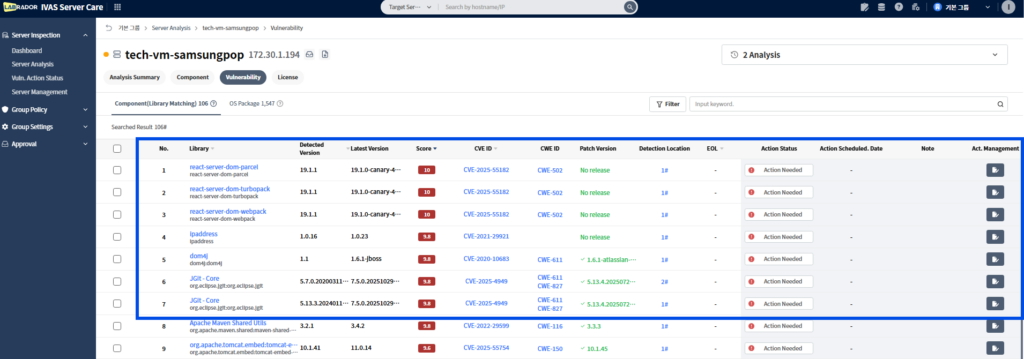
(Image caption: Labrador ServerCare detects vulnerabilities in live servers.)
To close this gap, Labrador Labs developed Labrador Server Care, a solution specifically designed to pinpoint vulnerabilities
in operating servers.
Here’s how ServerCare works:
- Automatically scans each server to collect its installed software, frameworks, and librarAutomatically scans each server to collect its installed software, frameworks, and libraries Analyzes their open-source component dependencies.
- Connects with global open-source vulnerability databases (CVE feeds) so that when new ones like CVE-2025-55182 (React2Shell) appear, it immediately identifies which servers are affected.
This makes cooperation between security and operations teams much simpler: - Security Team: “We found 12 servers affected by React2Shell, flagged as P1 priority.”
- Operations Team: “Let’s patch the 5 most critical ones this week.”
When a CVSS 10.0 RCE vulnerability appears, Server Care categorizes it as a top-tier critical risk, prompting immediate response.
In one case, a Labrador Server Care customer scanned 1,000 servers in just one hour, identifying systems exposed to vulnerabilities -a task that previously took days.
[ Can you answer this today? ]
React2Shell itself is serious, but the more important question is this:
“Can your organization identify, today, exactly which servers are exposed to React2Shell and how many there are?”
If your answer is no, it’s time to review your vulnerability management system for live environments.
Check now how high-risk issues like React2Shell are detected and managed in your operating servers together with Labrador Labs.
📌 Get started with Labrador Server Care today!
Phone: US Office +1 650-278-9253 (Mon–Fri, 9 AM–6 PM)
Email: contact@labradorlabs.ai (1:1 demo requests and pricing inquiries)

